by Dylan Nash
1. Purpose: The purpose of this report is to deliver an understanding of the ‘Layered Approach’ security model to mitigating and deterring a potential terrorist attack. This report will cover the following areas:
- What a Layered Approach or Security in Depth is.
- Why Security in Depth is important to a terrorist management plan.
- Identifying ‘Left and Right of Bang’ measures to assist in mitigating pre-attack and containing post-attack incidents.
2. Aim: To explain how security in depth, i.e. ‘The layered Approach’ can help to effectively create a more secure venue or assist in post incident recovery should an attack occur.
3. Security in Depth is not a new concept, creating in depth defences has been a method used for hundred if not thousands of years by militaries the world over in the pursuit of establishing a system that limits the ability of an offensive force to succeed when attacking. It is the act of establishing defensive layers to encumber anyone who has ill intent towards someone else or their assets.
Security in Depth (SID) refers to the multiple layers of security used to safeguard an asset. These security measures function in concentric layers, much like an onion, utilising a combination of different technologies and security operations to protect against physical threats and forced entries. (Adamo Security, 2020)
A prime example of this are strategically placed castles. Often times, these could be found on a hill, with an outer wall that could be defended by strong points, followed by an inner wall which is further developed with defendable positions. Between the outer and inner wall, there could be a moat or obstacle with controlled access and egress points. Within the inner wall, there could be the main structure (a Castle), which could have funnel points that requires a would be attacker to move into certain bottle-necks throughout the structure that could be further defended. By constructing a position in such a way, a defender has created a sequence of defensive layers that makes it more difficult for an attacker to be successful in their endeavour to accomplish their end state, taking the castle. In some instances, this in-depth security could even deter any attacker from attempting to attack in the first place, thus mitigating that risk.
This is the principal that modern day Security Risk Management (SRM) practitioners need to incorporate into SRM plans and protocols. By enabling a layered method to their security protocols, this not only can make it more difficult for a potential terrorist attack to be successful, but may deter the attacker from even attempting. However, the ‘Layered Approach’ must be part of a wider culture within the organisational culture. When this element harmoniously works in tandem with a functioning SRM process and Rational Choice Theory/Target Selection Process (RCT/TSP), there is more potential for a culture of security to foster within the overall organisation’s culture. This is accomplished through having total control of the greater territory owned by an organisation, understanding that everybody is responsible for SRM, and an understanding that everybody accepts responsibility for their own little piece of the owned territory and with an attitude of ‘not today and not on my shift’.
5. Left and Right of Bang is a term within the security community to identify pre and post incident measures and factors. Left of Bang (LoB) are the security measures employed in order to mitigate risk and possibly prevent/deter an attack from occurring. A layered system should be established and maintained prior to any sort of terrorist attack ever taking place. This will be accomplished through the use of multiple tools available to include, manned guarding, access/egress control points, stand-off distance, CCTV, secondary access/egress points, escape routes, signs, fencing, and air-lock systems. This is not an exhaustive list, but is meant to provide an idea of some of the many tools that can be used to create a layered system which establishes and identifies the boundary and territory owned by an organisation. The boundary is the first point of contact with anyone attempting to gain access to a defined area, the territory is the defined area owned by the security apparatus. The more layers and further distance that is created between a boundary (first point of contact) and the centre of what is being protected, the safer it is at that centre.
Because the security levels increase in line with the zones, you will be creating longer delays with each new layer you add. The cumulative delay gives you more time to respond to any attempts at unauthorised entry to the inner zones. (www.protectivesecurity.govt.nz , 2019)
Right of Bang (RoB) refers to the time following an attack or attempted attack. Even with the previously discussed security in depth apparatus in place, there is still potential for an attack to occur within that territory. This is due to the potential for holes withinr that apparatus (reference figure 1). However, having more layers in place and establishing that distance to the centre of the system enables a greater chance for damage from an attack to be minimised. By having several layers established, with distance between these layers, it be more difficult for an attacker to reach their intended target. For example, if a bomb is to be used in an attack, layered mitigation measures may divert or deny the appropriate access to an attacker. If the attacker is able to make it through one or two layers before they are identified, if the bomb were to explode, the damage created and likelihood of it having the maximum intended affect could be greatly reduced due to it being compartmentalised within that layer, thus potentially saving life and property.
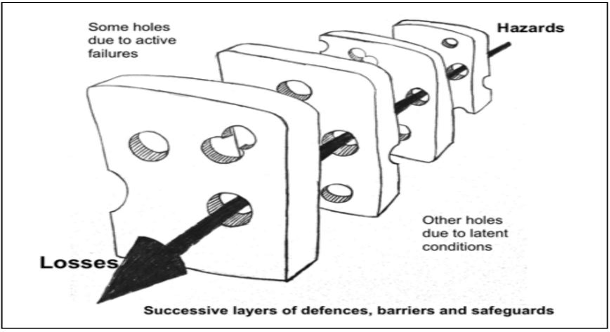
Conclusion: Understanding security in depth and the layered approach is important in being able to have a functioning terrorism management program in place for an organisation’s security apparatus. When a functioning layered approach to security is developed, maintained, reviewed, and bought into, the culture of security throughout an organisation’s overall culture improves. It enables all stakeholders at all levels, both internal and external to understand that their safety is a priority and that there is a process in place which allows them to operate within safe boundaries.
